The paradigm shift of work-from-home and security concerns
As the pandemic forces many employees to work from home, can your organization stay productive – and safe?
Work-from-Home or WFH, as we all call it, is becoming a household term as the COVID-19 pandemic continues to change the work-scape and forces organizations to mobilize their workforce to stay at home worldwide. Are organizations ready with the sudden change of work culture, system and security perimeter? Are service providers’ infrastructure able to cope with persistent high demand without cutting corners?

Uneven Preparation and Readiness
A recent poll shows that security preparedness is uneven as organizations make an unprecedented transition to remote working. About half (52 percent) said they are mostly prepared but with challenges on WFH strategies, 30 percent fully prepared, 13 percent somewhat ready to move minority of workforce/students to online platform; and 5 percent not ready at all.
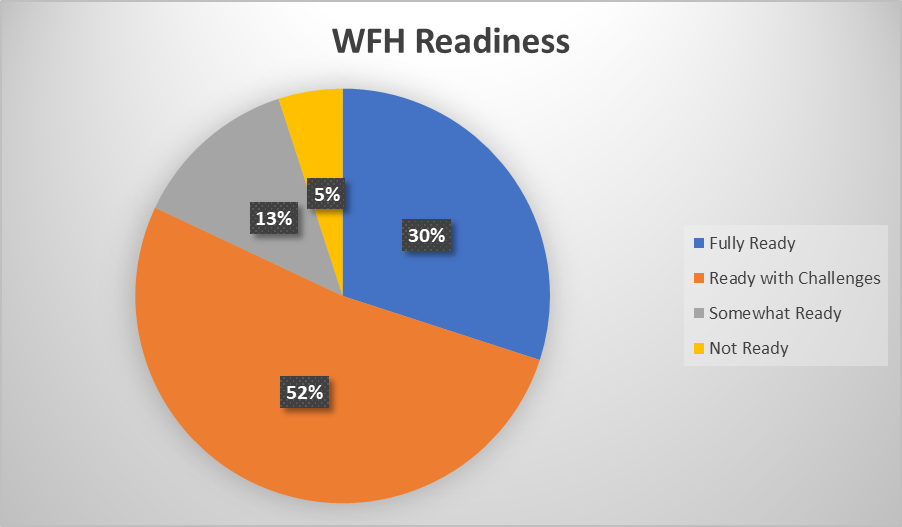
These stats come with a staggering 40 percent reported seeing more cyber attacks on their remote footprint. Not only it changed the threat-scape with increase surface of attacks to the home and public networks; it has given cybercriminals an unprecedented opportunity. The lack of training, knowledge and robustness of security in home and public environments has proven a challenge for IT department to protect and maintain.
Even more threats
Cyberthreats have always been a hot topic and have grown exponentially. Now, it is even more crucial to pay attention especially in this trying time. Let’s examine some of them.
Zoom Video Conferencing Tool: Security researchers has found a sharp rise (as many as 1,700) new domain names containing the word ‘Zoom’ registered. Many of those were found to be suspicious impersonating the genuine Zoom domains attempting to capture users’ personal details.

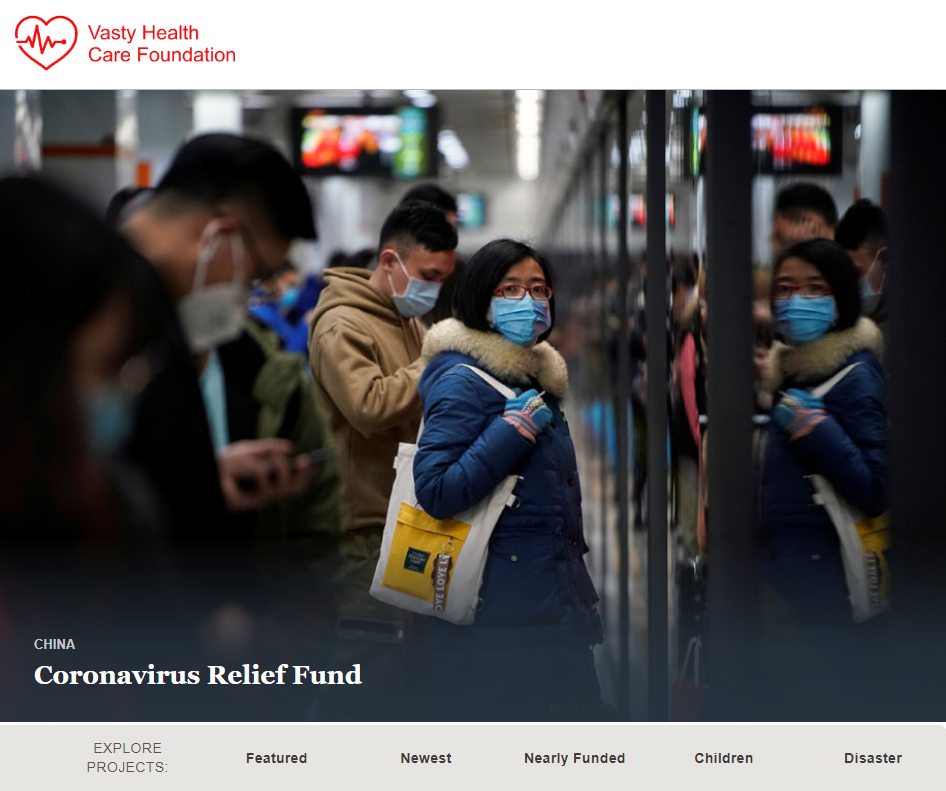
Vasty Health Care Foundation: Coronavirus Relief Fund. It was one of several fraudulent websites that recruit money mules to prey on human kindness in the name of helping Coronavirus victims. The content of the website is copied from globalgiving.org
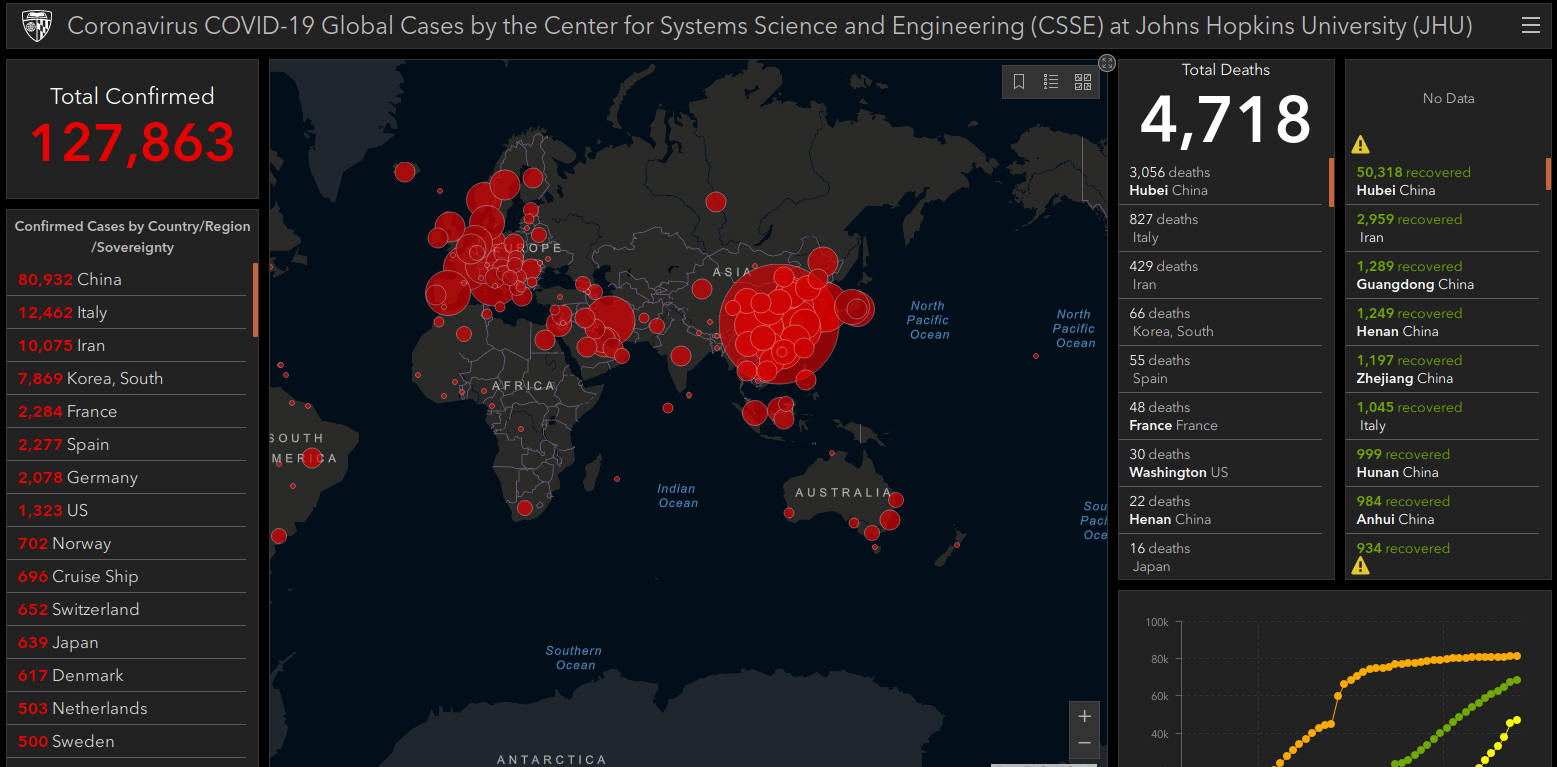
Cybercriminals constantly latch on to news that captivates public attention, but usually they do so by sensationalizing the topic with misleading information. This time, however, cybercrooks are disseminating real-time, accurate information about global infection rates of the pandemic from Johns Hopkins in a bid to infect computers with malicious software.
Easy to implement WFH? Think again.
For modern and high-tech companies such as Microsoft and Apple, remote work is their second nature versus smaller companies and organizations, however, it is a shock to their work culture and system as employees are suddenly forced into the new reality. The infrastructure and policies in place are simply not well-thought out, planned and executed. Therefore, they are often left with huge security risks with virtually no mitigation steps as they build infrastructure from the get-go.
For the past few weeks since the government mandated shutdown, our team has been working round the clock helping organizations for WFH initiative. We do so with cybersecurity risks associated in mind.
Six common challenges organizations are facing:
- Managing physical security of corporate owned devices.
- Are home networks secure? What’s in a home network?
- Do work from home users really need to access the corporate network?
- Authorization using conventional means such as via phone or video call.
- Virtual training and learning, reskilling and upskilling.
- Do you have a robust support program and crisis management in place?
We often work with business analysis professionals to help business owners and stakeholders to understand, outline problems (risks), identify opportunities (mitigate those risks with controls) and provide a technology solution that is aligned with their business objectives and goals.
If you are looking to learn how cybersecurity analysis can help your organization mitigate risks learn more about the new Cybersecurity Analysis Learning and Certification Program developed jointly by IIBA and IEEE Computer Society.
Get the credibility of a joint certification and learn key cybersecurity concepts and tools business analysis professionals need today.
Start Now
About the Author:
Chee Lam, is the CEO and founder of Deskflix Inc. with offices in Toronto and Vancouver, helping private equity businesses with specialized investment management services such as Business Continuity Planning, Cyber Security, investors DDQ sessions and advisory.
You can contact him by email at clam@deskflix.com or add him through Facebook https://www.facebook.com/lamlamz